WHAT YOU CAN DO
ABOUT DATA RETENTION
About Data Retention
The Australian Federal Parliament voted to give law enforcement and intelligence agencies access to an unprecedented
amount of information on all Australians.
![]() The Coalition Government and Australian Labor Party goose-stepped together to pass legislation requiring telecommunications service providers to store enormous
amounts of personal data of every Australian for a minimum of two years under the mandatory data retention scheme.
The Coalition Government and Australian Labor Party goose-stepped together to pass legislation requiring telecommunications service providers to store enormous
amounts of personal data of every Australian for a minimum of two years under the mandatory data retention scheme.
This data retention scheme takes effect on October 13, 2015.
See here: "Data regime will see us funding our own surveillance", Leanne O'Donnell, 08/10/2015 ![]() for a good recent overview of the scheme.
for a good recent overview of the scheme.
This creates a mass surveillance regime that will target all Australians at a time when other countries have abandoned this approach,more info and Australians will likely pay for this increased surveillance through taxes and additional phone and Internet charges. This is despite overwhelming evidence that mandatory data retention schemes do not work to reduce serious crime and are a substantial assault on privacy.
This page contains an overview of what this is and what it means to you (also, there are some handy videos to watch and share as well).
For example:
- The UK, much touted by AG Brandis as an example to follow, had it's data retention regime struck down by the courts: https://delimiter.com.au/2015/07/20/uk-court-strikes-down-data-retention-bill/

- In 2014 the European Court of Justice has overturned Europe's data retention directive, arguing that it's disproportionate and a violation of people's privacy: https://torrentfreak.com/eu-court-overturns-data-retention-directive-140408/

Video Overviews
What is Data
Retention and
why does it
matter to you?
What is Data Retention and why does it matter to you?
- The Abbott government and ALP formed a unity ticket to pass the Data Retention Legislation, avoiding the need to negotiate with the crossbenches and thus limiting their ability to negotiate on extra safeguards or on limiting the bills scope.
- What does this mean?
- All information about your communications are now required to be stored for at least 2 years.
- This includes, but is not limited to, what you do online, who you speak to on the phone, where you go with your mobile phone, who you email and when, and so on.
- This is tantamount to carrying a tracking device on you 24/7.
- Using analysis software, intelligence & law enforcement agencies will be able to create a very detailed profile on you, your travels, your associates & relationships, interests & hobbies, personality and so forth.
- Government 'law-enforcement' agencies (ASIO, Australian Federal Police, ASIC, ACCC, Customs, and around 80 others)
will be able to access all this info, without even getting a warrant from a magistrate.
Define agencies?
The Legislation
 allows for the government to declare any agency a 'criminal law-enforcement agency' if its functions include:
allows for the government to declare any agency a 'criminal law-enforcement agency' if its functions include:
- enforcement of the criminal law; or
- administering a law imposing a pecuniary penalty; or
- administering a law relating to the protection of the public revenue.
- Why does it matter?
- This is a gross violation of your privacy.
- This treats all citizens as if they are criminals, guilty until proven innocent.
- This further undermines the trust relationship between our government and its people (if they don't trust us, why should we trust them?).
- This exposes all your personal information to potential misuse by law-enforcement agencies, the government or even hackers and criminals who manage to obtain the data.
- The costs of the scheme will result in increased internet and telephones charges that you will have to pay.
- This will have a chilling effect on free speech, and make future political change and protest far more difficult.
- See the "What is so bad about Data Retention" section below for more on these issues.

Does it include browsing history?
- Supposedly not, however the government has been very unclear on what their metadata definition actually includes and it can be easily expanded later to include content/browsing history.
- They say they don't want browsing history or content of communications, but there will be cases where it is difficult to separate the two.
- There is no explicit requirement that your service provider not store that information, just that they don't have to.
- It may, in some cases, be cheaper and easier to leave content & browsing history in the data retained, rather than take the effort to strip it out.
- Despite saying they don't want content or website browsing history, some of the data they will collect can reveal some of this information anyway.
- The "metadata" they say they want can often be more revealing
 than the actual content of the communication.
than the actual content of the communication. - Whatever claims politicians and bureaucrats have made about Data Retention need to be taken with a grain of salt because it seems in many cases they simply do not understand what they are taking about.


What is Metadata?
- Firstly Metadata is just Data. It is misleading to use the term in the way the government has, as if it is somehow more innocuous or less intrusive.
- Metadata is in fact very revealing.

-
See also: "What reporter Will Ockenden's metadata reveals about his life"
 for how revealing, and misleading, metadata can be.
for how revealing, and misleading, metadata can be.
-
See also: "What reporter Will Ockenden's metadata reveals about his life"
- To go by the official definition, it is data about data.
- Basically, it is the data that identifies your communications - the how, what, where, when, and to whom you communicate with.
- The government analogy of 'the address on the envelope' minimises how revealing this metadata can be.
- The government's definition of what data is to be retained is vague, technically contradictory and goes well beyond the scope of what your telco currently keeps.
- Attorney-General George Brandis certainly has trouble defining it. Watch him fail spectacularly at explaining metadata in the video above.
- The legislative definition is here

- It includes, but is not limited to, subscriber of account holder information, sender and receiver of communications, date, time and duration of communications, location (including where you are when you use your mobile phone), what services is used (eg, voice, social media, Skype, SMS etc), and the type of delivery service (eg, ADSL, Wi-Fi etc) [1]
- "You know, metadata is a different kind of data but it actually is very intimate. If you call a suicide prevention hotline, it
doesn't matter what you say; it's the fact that you called them. Metadata reveals who we're intimate with, who we associate with,
what our interests are, who we are, what we are. And because it can be processed by computers automatically, it's not voice conversation,
it's just data. It allows people with access to that metadata to do very extensive levels of surveillance." - Bruce Schneier,
Lateline, ABC 10 March 2015

Brandis metadata fail Sky news interview
What is so bad about Data Retention?
- It undermines the legal principle of innocent until proven guilty. This treats every Australian citizen as a suspect by default.
- Agencies should have to get a warrant from a magistrate to access this information. Currently they only need approval of an authorised officer in their department.
- It greatly increases the power of policing, security & intelligence agencies over Australian society.
- There is great potential for abuse both by law enforcement agents accessing metadata and criminals targeting vast stores of personal data.
- There have been many cases of data retention being abused by law enforcement who have used the data to investigate love interests.
See 'LoveInt'

- Confidential Police, ASIO and Office of Police Integrity files were found in a drug raid in
Melbourne in 2010.

Examples like this show the grave risks of giving warrantless access of private data to law enforcement agencies. - It will impose a massive cost upon all Internet users in Australia; you will essentially be paying a big new "surveillance tax" (see the "So what will it cost?" section below).
- It will damage competition in the ISP/Telecommunications market as smaller service providers are less able to absorb the costs of complying with data retention laws. ("very real prospect of ISPs going out of business") (.pdf)

- It will make it harder for innovation within the sector in Australia as it introduces more red tape and barriers to providing internet/communications services in Australia. It is now more likely that
startups will need to relocate offshore.
- It will create massive 'honeypots' full of the private information of millions of Australians that will become an enticing target to criminals, identity thieves, foreign governments, and corporations:
- A data breach of this retained data will occur. It is not a matter of "if" but "when". Think about if you would like to allow you friends, family, employer, workmates, police or criminals to see everything you do online or see everywhere you go.
- This could expose you and your family to identity theft.
- This could expose you and your family to blackmail.
- This could threaten your employment prospects.
- This could put people at risk. Especially, for example, if they are police informants, witnesses to a crime, or escaping from violent ex-partners.
- This could embarrass people or expose private information. Think of the revealing of embarassing medical conditions, revelations of sexual preferences, or many other things people may prefer to keep private.
- This could reveal corporate or government secrets to foreign or competing interests.
- This could expose high level public servants, defence personnel or elected representatives to blackmail by foreign governments or criminal interests.
- The possibilities go on and on...
- It can result in numerous 'false positives' where innocent people have their lives ruined by having to defend themselves from accusations as a result of misinterpreting their metadata.
Innocent activities can look suspicious if viewed through a prism of assumed guilt.
See 'False Positive Paradox'

- It will have a chilling effect on free speech and prevent people from potentially seeking professional help in personal areas.
More on this?
From the Pirate Party "Submission to the Parliamentary Joint Committee on Intelligence and Security Inquiry into potential reforms of National Security Legislation", 2012, p4:
People under constant surveillance stop behaving like free people; to the detriment of society. Data retention plans similar to the proposed regime in the terms of reference have been enacted in Europe under the Budapest Convention on Cybercrime4 to widespread opposition, with legislation being rejected by Sweden and overturned in Germany, Romania and the Czech Republic as unconstitutional. In the German case the Judges determined that blanket surveillance could "cause a diffusely threatening feeling of being under observation that can diminish an unprejudiced perception of one's basic rights in many areas," as stated by the President of the Court, Hans-Jürgen Papier. They considered that "such retention represents an especially grave intrusion" into citizens' privacy5.
The German data retention regime, while it was implemented, had a negative impact upon people accessing online resources due to privacy concerns. Research institute Forsa found that one in two Germans would refrain from seeking help from professionals such as marriage and drug abuse counsellors and psychotherapists by telephone, mobile phone or email because of privacy concerns. One in thirteen people had already refrained from using telecommunications at least once due to data retention, which put the number at an estimated 6.5 million people6. The negative impact on the health and wellbeing of citizens caused by the lack of privacy should be reason alone to reject the data retention proposal.
See http://pirateparty.org.au/media/submissions/ppau-national-security-inquiry-submission.pdf

- Not only will Data Retention not fulfil its purported purpose of preventing terrorist attacks, it will potentially make us more vulnerable to terrorist attacks.
- It creates more "haystacks" to look for "needles" (ie potential terror plots) in, by increasing the amount of data that law enforcement agencies need to look at. Real dangers could thus get lost in the noise.
- It would be unable to prevent 'lone wolf' operators.
- Terrorist actors are generally known to police beforehand; targeted surveillance with a warrant not only suffices in these circumstances, but is a far better use of police resources.
- Terrorists are likely to be using technologies and practices that would cover their tracks and render mass retention of everyone's data useless anyway.
- There is much scope, for Scope Creep
- The AFP admitted that Data Retention could be used in tackling piracy.
- There are no protections to stop your metadata being exposed by a discovery process in civil litigations. Meaning that your personal details could be exposed in divorce proceedings, or any time that someone decides to sue you regardless of the outcome.
- The data to be retained is defined in regulations which means they can be changed without having to be approved by parliament.
- We can already see this scope creep before it is even enacted, with this example from the ATO: "Instant scope creep: Parliament recommends ATO data retention access", Delimiter, 08/09/2015

- It will damage Journalism and silence Whistleblowers
- The warrant access 'protections' for journalists added by Labor are not very strong.

- The AFP admits
 it doesn't need to access journalists data to find whistleblowers or leakers.
it doesn't need to access journalists data to find whistleblowers or leakers. - See this simulation
 by the Guardian to show how a journalist's source can be found via metadata requests.
by the Guardian to show how a journalist's source can be found via metadata requests. - Many potential whistleblowers will now refrain from doing so. This will have a very negative effect on the accountability of government departments and politicians.
- Journalists will have a much harder time protecting their sources, which in turn imparts a negative effect on the health of our democracy and media freedom.
- See also:
- The warrant access 'protections' for journalists added by Labor are not very strong.

So what will it cost?
- Estimates of how much Mandatory Metadata Retention will cost everyday Australians varies greatly
- The Prime Minister has suggested $400 million.
- iiNet however estimates $130 per customer per year.

- Costings by PricewaterhouseCoopers for the A-G Department says upfront costs are estimated at between $188.8 million and $319.1 million (they refused to publish
 the full report).
the full report). - The government Attorney-General claims less than $4 per customer per year.
- The details of funding arrangements, and government commitment to partially fund the scheme is unclear.
- It could have a very negative effect on the ability of small ISPs or internet services to compete.
- It amounts to a surveillance tax on every Australian, whether it be via increased internet costs passed on by ISPs, or taxpayer dollars.
- The financial costs are but one minor cost - the cost to our freedoms, privacy and civil liberties are far more grave.

But I have nothing to hide?
- "You know, the "nothing to hide" argument comes up again and again and it's obviously ridiculous. Privacy is not about something to hide.
Privacy is about human dignity. Privacy is about individuality. Privacy is about being able to decide when and how we show ourselves to other people." - Bruce Schneier,
Lateline, ABC 10 March 2015

- Rules can change: legal activites you enjoy, could become illegal in the future.
- It's not you who determines if you have something to fear: You may be innocent, but automated computer algorithms looking at your metadata,
or overzealous ASIO agents, may red flag you anyway by perceiving an innocent action as suspicious.
Despite being proven innocent, this event can ruin your life.
See Mohamed Haneef case
 and also 'False Positive Paradox'
and also 'False Positive Paradox' 
- Laws must be broken for society to progress: Imagine how far the US Civil Rights movement would have gotten if the FBI who opposed it
vociferously had access to the all pervasive metadata that would have been generated by organising that movement in the internet age. It may have never gotten
off the ground with the police always a step ahead of protesters and better able to blackmail leaders. We'd be stuck in a perpetual status quo with unfair laws
never being able to be effectively opposed.
See: "FBI's "Suicide Letter" to Dr. Martin Luther King, Jr., and the Dangers of Unchecked Surveillance"

- Privacy is a basic human need: People need privacy to be able to experiment with ideas, actions and thoughts and to be able to act without the fear of someone always looking over their shoulder.
Without privacy, people will check their speech and actions. More on this?
- Privacy is a fundamental human right. Article 12. on the Universal declaration of Human Rights says:
'No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence, nor to attacks upon his honour and reputation. Everyone has the right to the protection of the law against such interference or attacks.' - See also: Rick Falkvinge, "Debunking the dangerous
'If you have nothing to hide, you have nothing to fear"

- "Whether explicit or not, conceptions of privacy underpin nearly every argument made about privacy, even the common quip "I've got nothing to hide." ...
understanding privacy as a pluralistic conception reveals that we are often talking past each other when discussing privacy issues. By focusing more specifically
on the related problems under the rubric of "privacy," we can better address each problem rather than ignore or conflate them. The nothing to hide argument speaks
to some problems, but not to others. It represents a singular and narrow way of conceiving of privacy, and it wins by excluding consideration of the other problems
often raised in government surveillance and data mining programs. When engaged with directly, the nothing to hide argument can ensnare, for it forces the debate to focus
on its narrow understanding of privacy. But when confronted with the plurality of privacy problems implicated by government data collection and use beyond surveillance and disclosure,
the nothing to hide argument, in the end, has nothing to say."
- Daniel J Solove "'I've Got Nothing to Hide' and Other Misunderstandings of Privacy"


"There was of course no way of knowing whether you were being watched at any given moment. How often, or on what system, the Thought Police plugged in on any individual wire was guesswork. It was even conceivable that they watched everybody all the time. But at any rate they could plug in your wire whenever they wanted to. You had to live-did live, from habit that became instinct-in the assumption that every sound you made was overheard, and, except in darkness, every movement scrutinized." - George Orwell, 1984
What can you do about it?
- Unfortunately, it has passed the Senate, so unless there's some kind of magical turnaround, it is set to become law.
- At this stage, the best bet is to ensure the Liberal party and ALP know how unhappy you are about it.
- Make sure they know that they will hurt at the ballot box for trading away our freedoms so uselessly: Vote for parties that oppose Data Retention.
- Be sure to tell your friends and family. Share this page on social media. Perhaps even join the Pirate Party
 :-)
:-) - For the main part, now that it has passed, the best course is to make sure it is unworkable. The tools and methods on this page will help that.
- Above all, take action now to secure your privacy online:

What You Can Do
The new impending Data Retention regime in Australia puts you and your family's privacy at risk. To assist in preventing your personal information from falling into the wrong hands you should take action to protect yourself now. What follow is a simple guide to some sample technologies that can help protect your privacy.
For more in depth information on protecting your privacy that goes beyond this guide, a good starting point is the EFF's
"Surveillance Self Defence" ![]() site. In fact, many of the links below in regard to specific items will send you there.
site. In fact, many of the links below in regard to specific items will send you there.
Please note that this guide is intended for average everyday citizens desiring to take some action to protect
their metadata from the ubiquitous mass surveillance of the new Australian data retention regime. If you are a journalist,
a dissident, a whistleblower or political activist, or have some other higher order
threat model, ![]() then you should seek further more specific technical & professional advice than this guide.
then you should seek further more specific technical & professional advice than this guide.
But for an easily digestible overview of a range of options to minimise your risk from the incoming Australian Data Retention regime, see below.
How to protect yourself and your family from Data Retention
Web Browsing/Internet
Whether you are using your desktop computer, or a mobile device, you should protect your actions from indiscriminate surveillance. Despite claims that data retention does not intend to collect and store your browsing history, any interaction online that is not encrypted will leak private data about you, your activities and connections. The below options will go some way to protect your actions from some aspects of casual surveillance if set up correctly.
Important: How careful you are and what tools you choose to use will depend on decisions you make about your "Threat Model" ![]()
VPNs
- What is a VPN?
- VPN stands for Virtual Private Network.
- VPNs work by creating an encrypted tunnel between your computer and another server.
- Your ISP cannot read the traffic in this tunnel; they can only see that you are connected to the server and sending/receiving (encrypted) data.
- VPNs are widely used in business: they allow people working from home to connect to their office network securely, which is vital for people working with sensitive information.
- VPNs will also allow you to bypass website blocking from the government's new anti-piracy regime, including any sites that could be accidentally blocked due to
collatoral damage.

- VPNs can also be used to bypass geo-blocking restrictions. What does this mean?
Have you ever been watching YouTube and seen that "This video is not available in your country" message? That's geo-blocking. If your IP address showed you as coming from country where that video was allowed to be seen, you could watch that video, but for various licensing reasons you cannot. Aside from privacy benefits, getting around geo-blocking to access services that aren't available in Australia had traditionally been one of the key uses for VPNs! (and doing so is not illegal)

More info: https://www.choice.com.au/electronics-and-technology/internet/internet-privacy-and-safety/articles/bypass-geo-blocking
 http://www.zdnet.com/article/competition-review-supports-tackling-australia-tax/
http://www.zdnet.com/article/competition-review-supports-tackling-australia-tax/ 
For a more comprehensive censorship bypassing guide see here: http://en.flossmanuals.net/bypassing-censorship/
- Using a VPN is legal.

- Using a VPN
- The easiest way to use a VPN is to purchase a service from a VPN provider.
- The provider will manage the server and will usually provide you with software and simple instructions on configuring your connection.
- Remember that a VPN provider outside of Australia would not be subject to Australian data retention requirements, but may still keep logs of your Internet use.
- While a little dated, this article may also be of help in further securing your VPN connection: http://torrentfreak.com/how-to-make-vpns-even-more-secure-120419/

- For discussions on VPNs and some tools to help test and use your VPN you may wish to try looking here: http://www.reddit.com/r/vpn

- Choosing a VPN
- Torrentfreak has provided a list of (self-proclaimed) anonymous VPN providers
in this article here.

- Crikey has a Aussie data retention specific guide to choosing a VPN here:
http://www.crikey.com.au/2015/03/24/keen-to-evade-data-retention-heres-how-to-choose-a-vpn/

- See also the EFF's SSD guide: Choosing the VPN That's Right for You:
https://ssd.eff.org/en/module/choosing-vpn-thats-right-you

- The above /r/vpn subreddit link
 may also be of use in choosing a VPN provider.
may also be of use in choosing a VPN provider.
- Torrentfreak has provided a list of (self-proclaimed) anonymous VPN providers
in this article here.
- Downsides & caveats to a VPN
- You will need to pay monthly fees (although often not very high).
- It can be slower - your traffic is routed through a server outside of Australia.
- Content unmetered by your ISP will count towards your monthly quota.
- Your traffic is only protected until it reaches the server. Instead of trusting your ISP, you are trusting the VPN provider: a disreputable provider could still log and monitor your traffic.
- It only protects data in transit: if your computer is compromised (e.g. by a virus or snooping software), your data will still be vulnerable.
- Loss of localised experience: some websites such as Google serve up different content based on your location. When your VPN is located outside of Australia, many websites may behave differently. For example, if using a German VPN connection, a website may give you its German language version.
- Note: protecting yourself from the Australian data retention regime is not the same as protecting yourself from NSA programs.
What does this mean?
There are a range of NSA programs such as PRISM
 which collect data from various social media and internet services. This can mean that once you log into a website like Facebook or Google,
you could be traceable back to your point of origin utilizing the NSA's PRISM system and other voluntary agreements with the US and other Governments,
due to the secretive nature of the systems and the revelations via whistleblower leaks, it would be prudent to assume this data accessible by Australian
Authorities. Your level of caution or paranoia on this issue should relate to your threat model. For an average user, this could be an acceptable risk.
For a dissident, activist or whistleblower you may wish to exercise more caution. Such as ensuring you never log into one of these services while using your VPN.
(Note: if your actions are high risk enough that your freedom or life depends on your anonymity, then you should be using a more complex guide
to your security than those available on this page)
which collect data from various social media and internet services. This can mean that once you log into a website like Facebook or Google,
you could be traceable back to your point of origin utilizing the NSA's PRISM system and other voluntary agreements with the US and other Governments,
due to the secretive nature of the systems and the revelations via whistleblower leaks, it would be prudent to assume this data accessible by Australian
Authorities. Your level of caution or paranoia on this issue should relate to your threat model. For an average user, this could be an acceptable risk.
For a dissident, activist or whistleblower you may wish to exercise more caution. Such as ensuring you never log into one of these services while using your VPN.
(Note: if your actions are high risk enough that your freedom or life depends on your anonymity, then you should be using a more complex guide
to your security than those available on this page)
See also Threat Modeling
- VPNs, while very useful and possibly one of the best front-line defences against data retention are not a magic bullet.
For example
Note that the legislation requires mobile internet providers to log each connection your phone makes, and the location of your device as it makes that connection. On a modern "smart phone", with a VPN turned on, the phone will still make frequent connections (on the order of every few minutes) to check email, push notifications, updates etc. and your location during each of these connections will be logged - there is nothing a VPN can do to protect you from the location-logging data retention issue.
In addition, please note that this guide is intended for average everyday citizens desiring to take some action to protect their metadata from the ubiquitous mass surveillance of the new Australian data retention regime. If you are a journalist, a dissident, a whistleblower or political activist, or have some other higher order threat model
 then you should seek further, more specific and more technical & professional advice than this guide.
then you should seek further, more specific and more technical & professional advice than this guide.
VPNs will likely not protect you from a concerted attack or targeted efforts
 against you specifically.
against you specifically.
- Creating your own VPN
- Unless you are an expert user and know exactly what you are doing, we would not recommend creating your own VPN.
- Personally created VPNs may very well suit some people's use cases, with these people being happy to make some compromises:
- Keep the server and all its software updated, and if necessary spend time recovering from breakages.
- Generate and keep secure very strong certificates and keys.
- Know that they're easily identifiable, should someone in their host country be listening.
- Be comfortable knowing they aren't able to physically secure the server running their VPN.
- You will however at least know for sure that the VPN company isn't keeping and sharing the logs with the NSA or ASIO, since the 'company' will be you. However this presumes any third party servers you use, or your own systems are secure and not compromised.
- As unlikely as it is, content companies would love the government to ban the use of VPN service providers.

- If you insist on trying it, here's a guide:
https://www.webdigi.co.uk/blog/2015/how-to-setup-your-own-private-secure-free-vpn-on-the-amazon-aws-cloud-in-10-minutes/
 - But do so at your own risk, and do your research.
- But do so at your own risk, and do your research.
Tor
- Tor stands for The Onion Router.
- https://www.torproject.org/

- Tor uses a wide network of voluntarily participating nodes to distribute your traffic to a number of anonymized exit nodes.
- i.e. it Tunnels your browsing through several other nodes.
- Makes it harder for someone to monitor your activities.
- Is censorship-resistance due to how the protocol works.
- Here's a Guide for Installation and usage: https://ssd.eff.org/en/module/how-use-tor-windows

- Warning! There are some things Tor does not do. It:
- Does not guarantee anonymity.
- Does not protect you from unencrypted communication tampering at exit nodes.
- Does not do operational security
 for you.
for you. - Tor can be slow.
What does this mean?
Due to its voluntary nature, whilst it is free and generally reliable it can be slow, frustratingly so, and is not recommended for high volume transmissions like file transfers, peer to peer (torrents) and the like. It is recommended to limit Tor use to web browsing if possible and to stuff you really wish to keep private. Because Tor is relayed through many extra locations and countries to disguise the true source of travel the distance travelled by the data is greater and goes through more 'hops' to get to you.
A more detailed explanation is here:
https://www.torproject.org/docs/faq.html.en#WhySlow
- It's not particularly safe to log in to your regular services with Tor, as the "Exit nodes" are impossible to trust with any of your credentials. Tor is for anonymous browsing, not every-day browsing that you want to keep private.
- Tor is also available for Android mobile devices:
- It is available for Android tablets and phones ONLY, via the Orbot package available on the Android Market. https://play.google.com/store/apps/details?id=org.torproject.android

- Tor is NOT available for iOS Tablets and Phones, and any app you see on Apple's App Store claiming to be a Tor client at this stage is most likely a dangerous fake.
- It is available for Android tablets and phones ONLY, via the Orbot package available on the Android Market. https://play.google.com/store/apps/details?id=org.torproject.android
- Note: please don't use Tor for data intensive activities like torrenting, streaming HD video or large innocuous downloads. Some people rely on Tor for their safety and protection from oppressive regimes and while more Tor users are useful, unnecessary congestion on the network could make things a lot more difficult for people who rely on it.
- Also: Use Tor at your own risk. Using Tor itself is enough reason to flag you for further attention from security agencies and could
increase the likelihood they may pay closer attention to your activities by presuming you have 'something to hide'.
-
If you are concerned enough about your privacy to use Tor you may also wish to consider using a specialised privacy protection oriented operating system, for example "Tails".
- What is Tails? It is a security focused Linux distribution which can be run from a DVD or USB drive.
- Wikipedia entry: https://en.wikipedia.org/wiki/Tails_%28operating_system%29

- Tails website: https://tails.boum.org/

Tor Animation video from
https://blog.torproject.org/blog/releasing-tor-animation
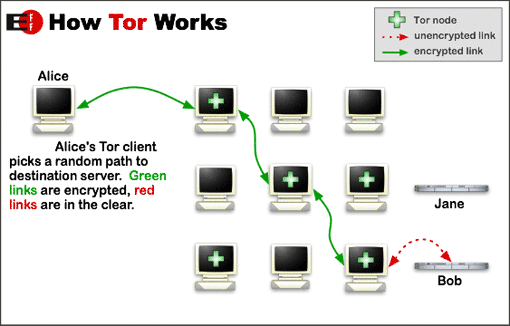
How Tor works diagram from EFF

Beyond the basics: More privacy protection tools
If you are worried about Data Retention, then you may also be concerned about other means by which companies, security agencies, governments and so on can track what you do and build a picture via your online activity.
Even if the current definition of what is to be retained under the data retention regime is limited to certain information, there is the likelihood that this definition will expand at a later date.
Additionally there is the threat that innocuous activity could inadvertently raise suspicion through false positive identification. This could in turn increase the amount of warrants issued on innocent people,
warrants which will then cause the retention of extra content in relation to these people.
Thus, average users could be more likely to come under the increased scrutiny of a
preservation order ![]() so protecting data that is outside the purview of the mandatory data retention regime may be advisable.
so protecting data that is outside the purview of the mandatory data retention regime may be advisable.
Keeping these expanded threats in mind, there are some other general tools and practices that you may also wish to start employing as a result of the new data retention regime and a general increase in surveillance of communication activities.
(Don't forget there are also the wide ranging NSA programs, copyright violation monitoring, censorship efforts, and criminal activities such as identity theft, in addition to our new domestic data retention regime).
This article from the Sydney Morning Herald gives a general overview of why just masking your IP address through a VPN may not be enough to protect you: Will Australia's metadata retention scheme track your digital browser fingerprints? ![]()

General Good Online Practice
- HTTPS
- HTTPS Everywhere.
- A simple browser extension made by the EFF.

- Will automatically push your browser to the HTTPS URL when a website supports HTTPS.
- This forces an encrypted connection when connecting to a website that supports such encryption.
- Guide for Installation and usage: https://www.eff.org/https-everywhere

- Mobile support is available for this extension only for the Firefox Browser, and only on Android devices.
- Ad-blocking
Note. This section is under review. Adblock has been sold
 and there are questions in regard to how much it should be recommended now due to the "acceptable ads" program
and there are questions in regard to how much it should be recommended now due to the "acceptable ads" program  and other reasons.
and other reasons. In the meantime uBlock Origin has been suggested as an alternative:
Adblock or Adblock plus.- These are Browser extensions.
- Despite name similarity, they are separate competing software products.
- Blocks popup ads, some ad banners and some tracking.
- Blocking ads and associated items like tracking cookies etc will cut down on the amount of 'metadata' you generate and assist in protecting your privacy.
-
Adblock: https://getadblock.com/
-
Adblock plus:https://adblockplus.org/
- Tracker Blocking
Note: tracker blocking plugins often break the functionality of image galleries, video playback, commenting/discussion systems and social media widgets. You may have to whitelist trusted websites.
- Ghostery
- An add-on for your browser which detects and blocks tracking which a website may be trying to do.
- Ghostery
 is proprietary, but cost-free.
is proprietary, but cost-free. - Available for all major browsers.
- Privacy Badger
- A browser extension for the Firefox and Chrome that will block all non-consensual tracking.
- Privacy Badger
 is open source, cost-free, a project of eff.org
is open source, cost-free, a project of eff.org  and in Beta.
and in Beta.
- As the Tor Browser is based on Firefox, Privacy Badger will also work with that.
- Disconnect
- A browser extension which blocks advertising, analytic and social media requests which are without consent.
- Disconnect
 is open source and cost-free. Disconnect also offer additional non-free services, like limited VPN access.
is open source and cost-free. Disconnect also offer additional non-free services, like limited VPN access. - Disconnect is available for all major browsers.
- Ghostery

The proposed Australian Data Retention regime does not purport to retain the contents of your email communication. Whereas the key methods for protecting your email communication will primarily protect the contents.
The proposed Data Retention regime will however potentially store the time you send an email, to whom you send it, what path it travels to get there, from where you sent it and the subject. The means of protecting this information starts to get beyond the scope of this site/guide.
While one could argue it is not 'necessary' to protect the contents of all your email with the below methods, you should always be aware of the potential for harm should the contents of emails become public or fall into the hands of unintended recipients (especially emails that contain sensitive information). Keep in mind that there are also a range of other government programs outside of Australia that may seek to obtain your email contents. However the encryption of all your emails, especially for an average user, could be considered overkill. Your levels of desired protection should reflect your threats and the contents of your emails.
For the various reasons detailed above, we will not go into too much detail on protecting email. But due to common queries about protecting emails, we provide some information and links below.
PGP
- PGP stands for "Pretty Good Privacy", and its main feature is encrypting messages (although it can do a lot more).
Its most common use is to encrypt the content (but not the metadata) of emails,
turning an email from
this
to
this.
- A more detailed explainer on what PGP is and what in can and cant do is available here:
https://ssd.eff.org/en/module/introduction-public-key-cryptography-and-pgp

- How to guides for setting up PGP:
- How to: Use PGP for Windows PC: https://ssd.eff.org/en/module/how-use-pgp-windows-pc

- How to: Use PGP for Linux: https://ssd.eff.org/en/module/how-use-pgp-linux

- How to: Use PGP for Mac OS X: https://ssd.eff.org/en/module/how-use-pgp-mac-os-x

- How to: Use PGP for Windows PC: https://ssd.eff.org/en/module/how-use-pgp-windows-pc
- A more detailed explainer on what PGP is and what it can and cant do is available here: https://ssd.eff.org/en/module/introduction-public-key-cryptography-and-pgp

Other services
Technically if you use an offshore webmail provider such as gmail, your data will not be included in the data retention regime, whereas if you use your local ISP email services it will be.
Anyone can see the issue with this insofar as any purported effectiveness of the data retention regime. However, don't forget that many services such as gmail may be accessible to Australian authorities via information sharing agreements with US agencies as part of the five-eyes surveillance programs. Also note, that if you use your foreign hosted email to email someone using an Australian hosted service, then that metadata will be available via retention of your recipents data.
This is an ever changing area as email services come and go, and so we will not provide any specific product or service recommendations here since what is ostensibly safe today, may not be tomorrow. If your personal threat model requires security of your email contents and metadata then we suggest you get further advice beyond this guide.
Some general information, articles of note are provided below:
- "Aussie email provider FastMail says it is exempt from Data Retention law", Delimiter, 8/10/2015

- "Use encryption and overseas email to beat data retention, says Ludlam", SMH, 25/03/2015

- "Can You Retain Your Privacy Despite Government Metadata Retention?", The Conversation, 30/03/2015

- "Metadata laws to be introduced on Tuesday, but there are still some unanswered questions", News.com, 08/10/2015

- "The Only Email System The NSA Can't Access", Forbes, 19/05/2014

Encrypted Phone Calls
There are a number of services like Wickr ![]() (as used by Malcolm Turnbull recently, he has
since moved on
(as used by Malcolm Turnbull recently, he has
since moved on ![]() to Signal) which provide endpoint to endpoint encryption;
or encryption between their servers and all endpoints. These provide an unknowable level of protection and it cannot be guaranteed that there are no backdoor agreements
between these services and any governments.
to Signal) which provide endpoint to endpoint encryption;
or encryption between their servers and all endpoints. These provide an unknowable level of protection and it cannot be guaranteed that there are no backdoor agreements
between these services and any governments.
One should be especially careful when using a service that does not run on open source or freely auditable code as you are placing trust entirely within the organisation to deliver what they advertise. There have been examples where a company claims to protect your security and privacy have been found wanting when exposed to closer scrutiny.
The value of these services is often pinned on your trust of the company in question. The below apps are widely considered the best options at this time (but make your own judgement call).
for Android
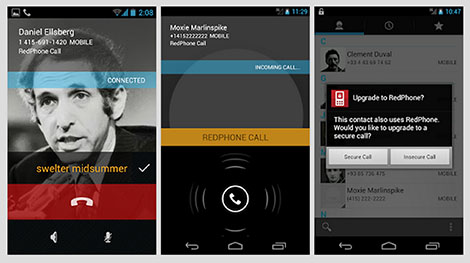
- Redphone
- Android mobile app that allows for encrypted voice calls.
- Uses wi-fi or data connection.
- Allows you to use your mobile phone number.
- Made by Open Whisper Systems.

- Free and open source!
- Uses end-to-end encryption, forward secrecy.
What does this mean?
End-to-end encryption (E2EE), which is non-certified or uncertified, is a digital communications paradigm of uninterrupted protection of data traveling between two communicating parties without being intercepted or read by other parties except for the originating party encrypting data to be readable only by the intended recipient, and the receiving party decrypting it, with no involvement in said encryption by third parties. The intention of end-to-end encryption is to prevent intermediaries, such as Internet providers or application service providers, from being able to discover or tamper with the content of communications. End-to-end encryption generally includes protections of both confidentiality and integrity.
http://en.wikipedia.org/wiki/End-to-end_encryption
In cryptography, forward secrecy (FS; also known as perfect forward secrecy, or PFS and also key erasure) is a property of key-agreement protocols ensuring that a session key derived from a set of long-term keys cannot be compromised if one of the long-term keys is compromised in the future.
http://en.wikipedia.org/wiki/Forward_secrecy
- Note: Can only encrypt calls between two RedPhone users (or RedPhone and Signal users).
- Familiar interface, get from the Play Store.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-use-redphone-android
for Apple iOS
- Signal
- iOS mobile app that allows for encrypted voice calls and texts.
- Made by the same group as RedPhone (Whisper Systems
 )
) - Free and open source!
- Compatible with RedPhone on Android.
- Uses wi-fi or data connection.
- Allows you to use your mobile phone number.
- Get it from the Apple App Store.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-use-signal-–-private-messenger
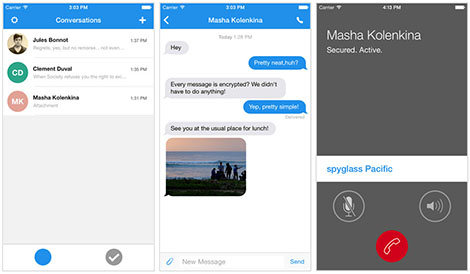
Encrypted Text Messaging
for Android
- Text Secure
- Secure Text Messaging app for Android - use your mobile to send encrypted, secure messages to another TextSecure user.
- Made by the same group as RedPhone and Signal (Whisper Systems
 ).
). - Uses end-to-end encryption, forward secrecy What does this mean?
- Can use it as your default texting app.
- Will store your messages encrypted on your phone.
- Encrypts where possible.
- Get it from the Play Store.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-use-textsecure-android
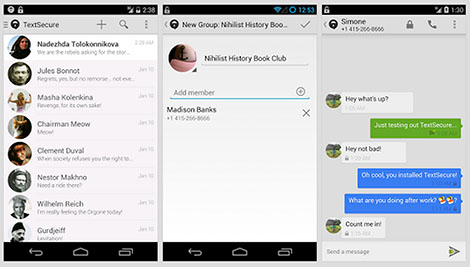
for Apple iOS
- Signal
- Signal 2.0 has recently been released for iOS that now includes TextSecure support.
- More information: https://whispersystems.org/blog/the-new-signal/

- Get it from the Apple App Store.
- Note that they are phasing out support for encryption for traditional SMS/MMS,
so if you use signal to send standard SMS text messages they will not be encrypted.
But you can get the same functionality by using Signal to send and receive "TextSecure" messages in encrypted formats.
More info: https://whispersystems.org/blog/goodbye-encrypted-sms/ So please make sure you are aware of which version you are using and what it does and doesn't encrypt.
So please make sure you are aware of which version you are using and what it does and doesn't encrypt.

Other options
- The Electronic Frontier Foundation have released a Secure Messaging Scorecard
 for voice and text messaging apps.
for voice and text messaging apps. - Telegram
 rates well on this scorecard,
and is open source, cost free and available on all for all major mobile and desktop operating systems.
rates well on this scorecard,
and is open source, cost free and available on all for all major mobile and desktop operating systems. - There are also proprietary and for-fee services available, like that offered by Silent Circle.

Encrypted Instant Messaging
for Windows/Linux
- Pidgin + OTR Plugin
- Open source "universal chat client".
- Can be used with Google Hangouts/XMPP, Yahoo, and apparently Facebook accounts.
- With OTR you get end-to-end encryption and forward secrecy. What does this mean?
- Note that OTR is a separate plugin that you need to obtain separately and add to Pidgin.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-use-otr-windows
- Note: OTR will not provide secure end-to-end encryption if you're the only one using it. Make sure those you talk to also install the plugin.
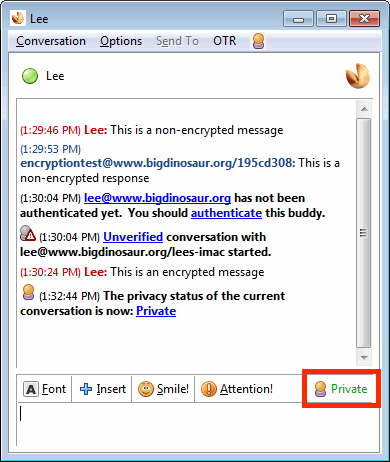
for Apple OSX
- Adium + OTR Plugin
- Adium is a free and open source instant messaging client for OSX.
- It is based on the same core as Pidgin but has a shiny Mac interface.
- OTR is a protocol that will encrypt your conversations.
- With OTR you end-to-end encryption, forward secrecy. What does this mean?
- OTR comes built into Adium, you do not have to install it as a separate plugin.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-use-otr-mac
- Note: OTR will not provide secure end-to-end encryption if you're the only one using it. Make sure those you talk to also use OTR.
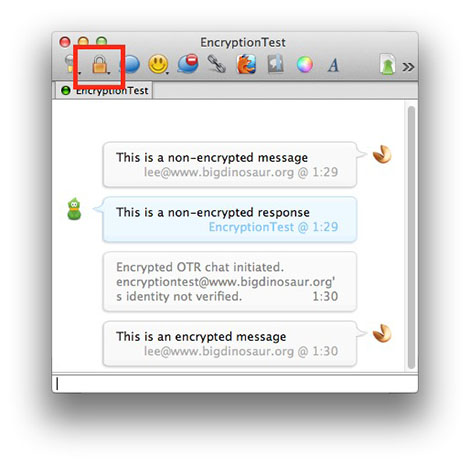
for Mobile (Apple iOS/Android)
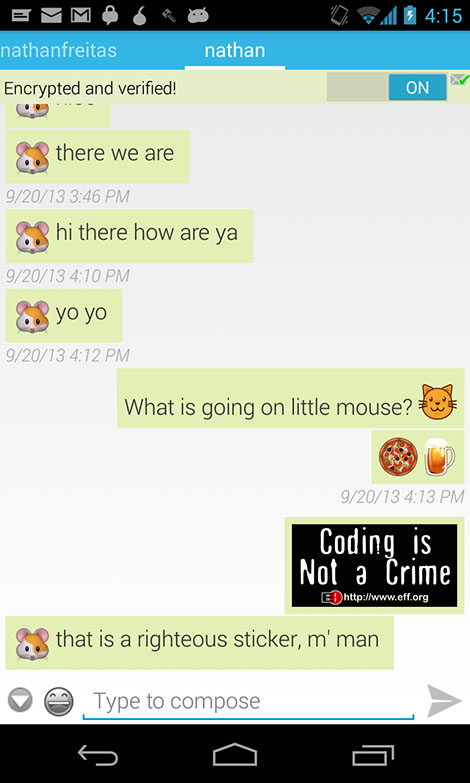
- Chatsecure
- Open source, XMPP client that supports OTR out of the box.
- OTR is a protocol that will encrypt your conversations.
- With OTR you get end-to-end encryption and forward secrecy. What does this mean?
- Get Chatsecure from Play Store or App Store.
- Guide for Installation and usage:
https://ssd.eff.org/en/module/how-install-and-use-chatsecure
Disclaimer: Note that all of the above products, options, tools and technologies are part of a fluid and everchanging field. The information above is accurate to the best of our knowledge at time of writing, however products change, technologies change, threats change. Securities get compromised and new best practices appear with regularity. Please view the above as a series of introductory options. You alone are responsible for your security and you should ensure you do your own research into the best options and tools for your own unique situation & needs. Please double check the current status of any of the above options before trusting them with sensitive communications.

Authorised by: D Judge, Party Secretary, Pirate Party Australia
65 Burg Street, East Maitland, New South Wales, 2323, Australia
Copyright © 2015 Pirate Party Australia 
This work is licensed under a Creative Commons Attribution 3.0 Unported License
This site does employ the use of analytics code so we can get an idea of traffic numbers etc... oh the irony. ;-P


